Whether deliberate or not, when you look around the many different websites, we think the subject matter has been made more complex than it needs to be. Sure, technology in this field continues to grow in order to meet trends and help consumers solve complex problems. The task of deciphering which system is best is not an easy one. After all, you only want to open a door…as simple as it may sound. So we’ve simplified our world so you can make informed decisions, to help you keep yours safe.
With that said, there’s really only two types of access control systems to consider: standalone or software driven. But as you’re about to discover, access control systems will do more than just open doors. Which of the two systems is going to be most suitable, will of course depend on what you want to achieve. Here’s a summary of the two.
Standalone systems – the door reader or door control unit controls the door entry system. So the programming of numeric pin no’s / cards / fobs is performed at every door. The system provides no identification or event reporting. It simply allows access when the user inputs or presents their ID to the door reader.
✓ Low cost security
✓ Ideal for small businesses
✗ Restricted control
✗ Security can be compromised
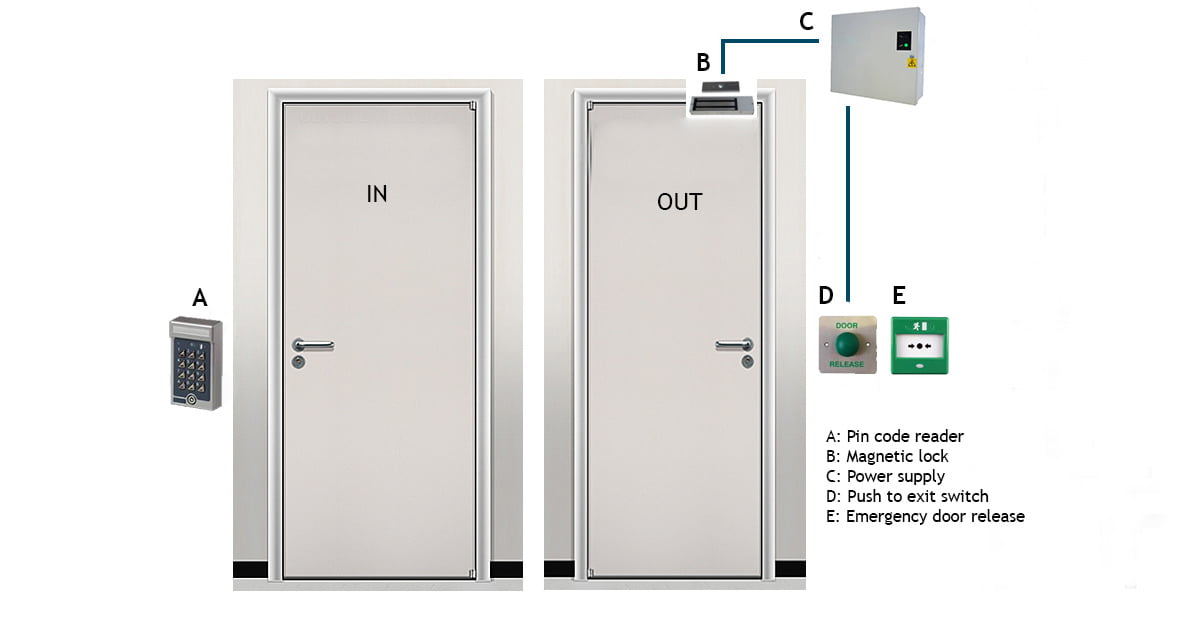
Illustration shows a standalone access control system installation. Comprising of keypad entry and push to exit switch.
Software-driven systems – all programming is done via a pc or web-based operation, allows you to identify and print daily activity reports of each individual by name. Some include features that allow the control of movement and access at certain times of the day and discourage card share or tailgating.
✓ Greater control
✓ Integration
✓ Remote operation (web-based)
✓ More secure
✓ Easily managed
✓ Can help reduce security budget (larger companies)
✓ Biometric options available
✗ Higher cost
Access reader options:
Pin code: A pin code is used to gain access
Cards / key fobs: Magnetic swipe cards (kept in wallet). Non-contact proximity cards (both usually kept in wallet) or key fob option (on key ring). Both use a built in chip referred to as Radio Frequency ID technology (RFID)
Biometric: Options include hand scanner, fingerprint & facial recognition
Pin code access reader / system – the most basic system employs a pin code reader where the same pin code is used & entered by staff in order to gain access. The pin code can be changed periodically. On the internal side of the door, a push-to-exit switch is generally used in order to leave the building. The exit switch is sometimes located in the reception if you want the receptionist to have control over it. More advanced readers do allow a limited number of unique pin codes to be issued (usually up to 50).
Unlike software driven systems, we see no benefit issuing multiple pin numbers when everyone can simply use the same pin code – as practiced by most organisations. This access control system is very popular with schools.
Cards / Key fob access reader / system – each card / key fob contains its own unique security code which is read by the reader. When presented to the reader the door lock releases to allow access. In this application, it does offer improved security over pin code as the code is hidden within the card. Though unlike pin code readers, readers using cards / fobs risk falling into the wrong hands. Lost cards can be deleted from the system but not re-issued.
Biometric access reader / system – most access control systems only offer fingerprint option. Provides the highest level of security compared to the other options. Fingerprint biometric readers should also include RFID or pin entry as a back up (pin entry is more secure), as the success rate of fingerprint technology is dependant on environmental factors and demographics. Manufacturers referred to this figure as False Acceptance Rate (FAR) usually given as a percentage based on test factors.
NB: With any of the above standalone reader options, a push-to-exit switch or a second door reader can be used to exit the building.
Pin code – in this environment, pin code readers becomes a far more attractive option, almost as good as biometrics in terms of security level. Provided the users preserve the integrity of the system by not revealing their pin number to anyone. Individual users are issued with a memorable pin number of choice. The software makes it possible to identify the person’s name via their pin number. In itself, this is a very simple, cost effective and secure security solution.
Cards / Key fobs – a card / key fob is used instead of entering a pin number. Programming of the software allows you to identify the card by the person’s name. It can be argued it’s more convenient and secure than pin numbers. Since each card has its unique identification number contained on a microchip within the card. The counter argument is that cards / fobs can of course be lost. In such an event, they can be quickly deleted on the software and a new one re-issued.
Biometric – as per our comment above for use in standalone systems, in addition, programming of the software allows you to identify the biometric scan by the person’s name. More advance software has the ability to significantly increase the success rate of these systems.
NB: With any of the above software driven reader options, a push-to-exit switch or a second door reader can be used to exit the building.
To summarise, plus some final guidance on choosing your access control system. Software driven systems compared to the standalone systems options discussed, allow you to identify anyone who’s entered the building or gained access through any internal door. If you use a push-to-exit switch (on a software driven system), the software will only record this as an event.
So with this configuration, the system won’t identify / record persons leaving the building. If this is required, the internal side of the door will require an additional door reader. Having a pair of door readers working together at each door, will literally open up a host of features & benefits, enabling you to take full advantage of the systems’ powerful capabilities.
To ensure installation complies with the guidance provided by the British Security Industry Association (BSIA). Designated doors leading to and on emergency exits must have an emergency break glass fitted and wired directly to the primary / lock circuit. So in the event of a fire or emergency, the activation of the break-glass will render the door in a permanent unlocked state. Standard practice is to fit units that also provides illumination plus an audible alarm when pressed.
Although called an emergency break-glass, modern units allow you to push on a piece of Perspex (rather than break an actual piece of glass), which is easily reset with the aid of a special key. You can also protect them using high-sounding alarm guards to deter tampering. So whether you opt for standalone or software driven systems, they all offer their own levels of security and effectiveness to suit your requirements.

Illustration shows a software driven access control system installation. Comprising of single proximity card / fob reader with push to exit switch. For more system options click on a door.
In taking access control systems to the ultimate level, many businesses and organisations have not realised the benefits of merging technologies together, and how they all come alive when used across multiple data platforms. We still look at systems as separate functions / solutions. Yet technology around us is moving towards integration, we can therefore expect further development in this area that allow analysis from all platforms e.g. CCTV to come together into one single source. Using AI learning algorithms will provide intelligent insights into the behaviours of personnel and day-to-day running of your organisation and even take appropriate action as necessary.
Below is a list of applications that could be integrated into access control systems providing multiple data streams, all feeding into one intelligent source taking security to another level.
Audit & Compliance:
Access control systems can be used to help facilitate auditing requirements. Record location (including denied access attempts) and time when users accessed the information for compliance purposes. Link to fire alarms to help manage and provide safe occupancy levels for fire regulation compliance.
Duty of Care:
Access control systems can be used to demonstrate duty of care by restricting access to dangerous or hazardous equipment, materials or locations or even walk-in freezers. And areas that are under construction or to personal assets such as locker rooms and staff only locations. Monitor working time spent at these hazardous locations. Protect lone workers and vulnerable staff from off-street walk-ins by unauthorised members of the public. Including children’s nurseries & schools and egress by unaccompanied minors. Ensure safety in and around workshops and swimming pools using supervised / logged escorted access by teachers. Similarly, restrict visitors / contractors into restricted areas.
Use access control systems to ensure more than one access credential is required for high-risk areas, to ensure individuals are not put at risk. Link HR information such as user credentials e.g. known health issues, blood group and emergency contact details etc.
Environment:
Perhaps the most overlooked is the environmental benefits of a well thought-out access control system, which can be used to control building occupancy, energy efficiency such as heating & lighting. Door monitoring systems can also be used to help reduce heat loss. Where an automated barrier system is used, a web-based system reduces carbon footprint and the need to visit sites that may be unattended.
Facilities Management:
Apart from day to day access management, access control systems can provide other essential support tools for facilities management teams. Additional benefits include monitor contractor hours. Ensure only trained personnel can gain access to sensitive / hazardous areas / tools etc. Assist with work permits. Manage access during holidays and non-business hours access, link into visitor management & fire roll call systems.
Health & Safety:
Enables restriction to areas and machinery where usage is dependant on training level and competency inline with health and safety objectives. Control access & exposure to hazardous areas. And restrict access to contaminated areas or areas that may be under construction.
Integration:
Access control systems can be integrated with a variety of systems to preserve security and increase control in the following applications:
IT systems / Personnel Management: Integrate with IT systems for central control and use active directory to manage users. Existing IT infrastructure can be utilised to reduce installation cost & minimise disruption. Access control is commonly integrated with time and Attendance to improve punctuality and reduce time labour management costs. Job costing systems provide job information, including time spent on job and costing etc.
Mitigate costs & losses:
In addition to the environmental impact (listed above) will also help reduce cost. Access control systems can reduce losses by securing assets including staff / property and potential health and safety claims. A safe working environment improves staff morale; the knock on effect is increased productivity and efficiency. Plus controlled usage of expensive printer toners / paper & other equipment. And link usage to cost centres. Monitor building occupancy to reduce costs and monitor contractor time on site.
Security:
Preoccupied with daily distractions etc. it’s difficult for companies especially those with a large workforce, to know who’s an employee (or visitor) and who isn’t. An access control system works 24/7 monitoring who goes where and when. Preventing unwanted strangers from entering your premises. Also provides controlled security during out of hours operation. Instant audit reporting of authorised persons and allowing or removing access rights. Perimeter security at access points can prevent walk-in theft and attack. Can be used to restricting access to company data. Plus reduces time / cost of replacing lost keys & locks if missing or stolen.
Under duty of care (above) we briefly mentioned schools & hospitals where access control systems can play other important and often overlooked roles.
Access control systems for schools can help support school education. Not only can they be used in libraries as tracking systems to help facilitate the safe return of books / school property etc. But also provide useful log reports for teachers that show how much time is spent in the library, or how many times over a given period students or pupils actually use the library facilities. Can also be used to help provide better insights into subjects that are of interest to pupils.
Access control systems for hospitals apart from offering protection for staff and patients, using no-touch points such as facial recognition systems, provide specialised uses that can be employed to Monitor, Control and Reduce (MCR) the risk of specimen contamination, and also the risk of spreading viral infections amongst staff & patients.
The daily comings and goings of hospital visitors poses another set of security risks. Even though they may well have checked in at reception. Maternity wards in particular can be made safer, by employing access control systems as a main, if not secondary security measure. Other uses of the system include limiting the number of visitors into the wards, or even refuse access altogether e.g. during out of hours or times of maintenance.
We've helped a multitude of business sectors, organisations including government institutions. Here's just a few of some well known names...

“Facetime provides a time & attendance system that ‘measures-up’ at Clarks flagship shoe shop at Street, Somerset”